Performance Routing (PfR) complements traditional routing technologies by using the intelligence of a Cisco IOS infrastructure to improve application performance and availability. PfR can select the best path for each application based upon advanced criteria such as, reachability, delay, loss, jitter, and mean opinion score (MOS).
PfR can also improve application availability by dynamically routing around network problems like black holes and brownouts that traditional IP routing may not detect. In addition, the intelligent load balancing capability of PfR can optimize path selection based on link use or circuit pricing.
Some of the scenario’s you could create are described on below links
Enterprise Intranet Solutions:
Internet Edge Solutions:
In this example we will demonstrate the rerouting of a Cisco Video IP Phone traffic based on Jitter criteria.
The setup is as follows:
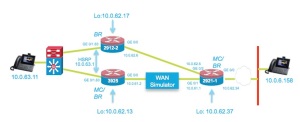
We use the ip sla functions of the router to verify the jitter behaviour of a WAN link between the 3925 and 2921-1 router.
As soon as the Jitter goes above a threshold the Voice/Video Traffic will be rerouted to an alternative link.
(Note: that you could allow all other traffic on the degraded link)
The following video shows the effect of Jitter on the phone, and the reaction off Pfr (timing can be tuned of course).
.
.
As mentioned in the video, you’ll see a change in routing behaveour, as example we’ll take the output off router 2921-1:
-Sep 3 17:16:19.358: %PFR_MC-5-ROUTE_EVENT: 50% of traffic classes controlled through policy VIDEO_VOICE 10 are NOT INPOLICY (trigger-log-percentage is 30%)
-Sep 3 17:17:19.382: %PFR_MC-5-ROUTE_EVENT: 100% of traffic classes controlled through policy VIDEO_VOICE 10 are INPOLICY (trigger-log-percentage is 30%)
-Sep 3 17:17:49.302: %PFR_MC-6-OOP_ACTIVE_MODE: Relative short term delay measurement is out of policy. Appl Prefix 10.0.63.11/32 N 17 [16384, 65535] [16384, 65535], delay 13, BR 10.0.62.34, i/f Gi0/1relative change 225, prev BR Unknown i/f Unknown
-Sep 3 17:17:49.502: %PFR_MC-6-ROUTE_EVENT_INFO: Appl Prefix 10.0.63.11/32 N 17 [16384, 65535] [16384, 65535]: route changed to BR 10.0.62.34, i/f Gi0/2, due to Jitter criteria. Out of policy reason: delay criteria
<- A route is injected in router 2921-1 for the IP Phone .11 (PBR)
Below you can find the key commands to configure above setup and some show commands to illustrate.
.
For additional examples do have a look at:
or
.
Basic Configurations:
Cisco 3925 ISRG2:
!
key chain key1
<- For secure communication between master & border
key 1
key-string cisco
!
pfr master
policy-rules VIDEO_VOICE
<- Defined specific rules for a specific application
logging
!
border 10.0.62.13 key-chain key1
interface GigabitEthernet0/0 external
link-group primary
<- Definition of the link- group, could be any name, linked to the pfr maps
interface GigabitEthernet0/1.63 internal
!
border 10.0.62.17 key-chain key1
interface GigabitEthernet0/0 external
link-group secondary
interface GigabitEthernet0/1.63 internal
!
no learn
<- Learning disabled
!
!
pfr border
local Loopback1
master 10.0.62.13 key-chain key1
active-probe address source interface Loopback1
!
!
!
interface Loopback1
ip address 10.0.62.13 255.255.255.252
!
interface GigabitEthernet0/0
ip address 10.0.61.2 255.255.255.240
duplex auto
speed auto
!
interface GigabitEthernet0/1
no ip address
duplex auto
speed auto
!
interface GigabitEthernet0/1.63
encapsulation dot1Q 63
ip address 10.0.63.3 255.255.255.0
standby 1 ip 10.0.63.1
standby 1 priority 150
standby 1 preempt
!
!
interface GigabitEthernet1/0
ip address 10.0.62.45 255.255.255.252
!
!
router eigrp 1
network 10.0.61.0 0.0.0.15
….
!
router bgp 65002
bgp log-neighbor-changes
neighbor 192.168.0.2 remote-as 65001
!
address-family ipv4
network 10.0.63.0 mask 255.255.255.0
neighbor 192.168.0.2 activate
exit-address-family
!
!
ip access-list extended VOICE_VIDEO_ACCESS_LIST
permit udp any range 16384 65535 host 10.0.6.155 range 16384 65535
permit udp any range 16384 65535 host 10.0.6.158 range 16384 65535
!
ip sla auto discovery
ip sla responder
<- IP SLA responder as well , to respond to probes of 2921-1
ip sla enable reaction-alerts
!
!
!
pfr-map VIDEO_VOICE 10
match traffic-class access-list VOICE_VIDEO_ACCESS_LIST
<- Match Voice & Video traffic
set mode monitor fast
<- Fast failover choosen
set resolve jitter priority 1 variance 5
set resolve delay priority 2 variance 50
set resolve loss priority 3 variance 50
set jitter threshold 100
set active-probe jitter 10.0.62.34 target-port 3050
<- Active Jitter Probe
set probe frequency 5
set link-group primary fallback secondary
<- link group fallback (primary and secondary can be any name)
!
control-plane
!
.
The 2921-2 Border Router
.
….
key chain key1
key 1
key-string cisco
!
!
!
pfr border
local Loopback1
master 10.0.62.13 key-chain key1
active-probe address source interface Loopback1
<- Used loopback as source for the Jitter probe packets
!
interface Loopback1
ip address 10.0.62.17 255.255.255.252
!
!
interface GigabitEthernet0/0
description WAN interface
ip address 10.0.62.6 255.255.255.252
duplex auto
speed auto
!
interface GigabitEthernet0/1
no ip address
duplex auto
speed auto
!
interface GigabitEthernet0/1.63
encapsulation dot1Q 63
ip address 10.0.63.2 255.255.255.0
standby 1 ip 10.0.63.1
standby 1 preempt
!
router eigrp 1
network 10.0.62.4 0.0.0.3
…
We do a show command off the Master Controller before change of jitter:
3925# sho pfr master
OER state: ENABLED and ACTIVE
Conn Status: SUCCESS, PORT: 3949
Version: 3.3
Number of Border routers: 2
<- Master controls 2 border routers
Number of Exits: 2
Number of monitored prefixes: 4 (max 5000)
Max prefixes: total 5000 learn 2500
Prefix count: total 4, learn 0, cfg 4
PBR Requirements met
Nbar Status: Inactive
Border Status UP/DOWN AuthFail Version DOWN Reason <- Both Border routers are active
10.0.62.17 ACTIVE UP 1w5d 0 3.3
10.0.62.13 ACTIVE UP 1w5d 0 3.3
….
Default Policy Settings:
backoff 90 900 90
delay relative 50
holddown 90
periodic 90
probe frequency 56
number of jitter probe packets 100
mode route control
mode monitor both
loss relative 10
jitter threshold 1000
mos threshold 3.60 percent 30
unreachable relative 50
trigger-log percentage 30
Learn Settings:
current state : DISABLED
<- We disabled learning in this example, going for fast failover
….
We’ll now look at the traffic-classes defined, seen we disabled
learning and enabled only 1 application prefixed (Voice/Video)
(only 2 traffic-class are defined).
One could use Netflow or NBAR2 to profile traffic.
c3925H#sho pfr master traffic-class
OER Prefix Statistics:
Pas – Passive, Act – Active, S – Short term, L – Long term, Dly – Delay (ms),
P – Percentage below threshold, Jit – Jitter (ms),
MOS – Mean Opinion Score
Los – Packet Loss (percent/10000), Un – Unreachable (flows-per-million),
E – Egress, I – Ingress, Bw – Bandwidth (kbps), N – Not applicable
U – unknown, * – uncontrolled, + – control more specific, @ – active probe all
# – Prefix monitor mode is Special, & – Blackholed Prefix
% – Force Next-Hop, ^ – Prefix is denied
DstPrefix Appl_ID Dscp Prot SrcPort DstPort SrcPrefix
Flags State Time CurrBR CurrI/F Protocol
PasSDly PasLDly PasSUn PasLUn PasSLos PasLLos EBw IBw
ActSDly ActLDly ActSUn ActLUn ActSJit ActPMOS ActSLos ActLLos
——————————————————————————–
10.0.6.155/32 N N udp 16384-65535 16384-65535 0.0.0.0/0
INPOLICY @6 10.0.62.13 Gi0/0 PBR
U U 0 0 0 0 0 0
2 2 0 0 0 0 0 0
10.0.6.158/32 N N udp 16384-65535 16384-65535 0.0.0.0/0
INPOLICY @37 10.0.62.13 Gi0/0 PBR
<– Detected application, in policy exiting GE 0/0
U U 0 0 0 0 178 178
2 2 0 0 0 0 0 0
The active probe:
sho pfr master active-probes forced:
OER Master Controller active-probes
Border = Border Router running this Probe
Policy = Forced target is configure under this policy
Type = Probe Type
Target = Target Address
TPort = Target Port
N – Not applicable
The following Forced Probes are running:
Border State Policy Type Target TPort Dscp
10.0.62.17 ACTIVE 10 jitter 10.0.62.34 3050 defa
10.0.62.13 ACTIVE 10 jitter 10.0.62.34 3050 defa
After the rerouting off the traffic. Use a other sho command to illustrate on the 3925:
sho pfr master traffic-class performance
=============================================================
…..
Traffic-class:
Destination Prefix : 10.0.6.158/32 Source Prefix : 0.0.0.0/0
Destination Port : 16384-65535 Source Port : 16384-65535
DSCP : N Protocol : udp
Application Name: : N/A
General:
Control State : Controlled using PBR
Traffic-class status : INPOLICY
Current Exit : BR 10.0.62.17 interface Gi0/0, Tie breaker was None
Time on current exit : 0d 0:8:2
Time remaining in current state : @59 seconds
Traffic-class type : Configured
Improper config : None
Last Out-of-Policy event:
No Out-of-Policy Event
Average Passive Performance Current Exit: (Average for last 5 minutes)
Unreachable : 0% — Threshold: 50%
Delay : 0% — Threshold: 50%
Loss : 0% — Threshold: 10%
Egress BW : 1033 kbps
Ingress BW : 1030 kbps
Time since last update : 0d 0:0:28
Average Active Performance Current Exit: (Average for last 5 minutes)
Unreachable : 0% — Threshold: 50%
Jitter : 0 msec — Threshold: 10000 msec
Delay : 80% — Threshold: 50%
Loss : 0% — Threshold: 10%
Last Resolver Decision:
BR Interface Status Reason Performance Threshold
————— ———— ———— ———— ———– ———
10.0.62.13 Gi0/0 Eliminated Jitter N/A N/A
10.0.62.17 Gi0/0 Best Exit Jitter N/A N/A
.
The Central router 2921-1
.
(has also pfr enabled)
!
!
key chain key2
key 1
key-string cisco
!
!
pfr master
policy-rules VIDEO_VOICE
logging
!
border 10.0.62.34 key-chain key2
<- Only 1 border router this time, with 2 external interfaces
interface GigabitEthernet0/2 external
link-group secondary
interface GigabitEthernet0/1 external
max-xmit-utilization percentage 100
link-group primary
interface GigabitEthernet0/0 internal
!
no learn
…
!
pfr border
local GigabitEthernet0/0
master 10.0.62.34 key-chain key2
!
!
interface Loopback0
ip address 10.0.62.37 255.255.255.252
!
interface GigabitEthernet0/0
ip address 10.0.62.34 255.255.255.252
duplex full
speed 1000
!
interface GigabitEthernet0/1
ip address 10.0.61.1 255.255.255.240
duplex auto
speed auto
!
interface GigabitEthernet0/2
ip address 10.0.62.5 255.255.255.252
delay 20
duplex auto
speed auto
!
!
router eigrp 1
network 10.0.61.0 0.0.0.15
….
!
!
ip access-list extended VOICE_VIDEO_ACCESS_LIST
permit udp any range 16384 65535 host 10.0.63.11 range 16384 65535
!
ip sla auto discovery
ip sla responder
ip sla enable reaction-alerts
!
!
!
pfr-map VIDEO_VOICE 10
match traffic-class access-list VOICE_VIDEO_ACCESS_LIST
<- This time ip phone .11
set mode route control
set mode monitor fast
set resolve jitter priority 1 variance 5
set resolve delay priority 2 variance 50
set resolve loss priority 3 variance 50
set jitter threshold 120
set active-probe jitter 10.0.63.1 target-port 3050
set probe frequency 5
set link-group primary fallback secondary
!
…
Have fun!
Johan De Ridder
Filed under: Borderless Networks | Leave a comment »








![[fig. 1] ucv6_srv_cfg ucv6_srv_cfg](https://tblogbelgium.files.wordpress.com/2011/02/ucv6_srv_cfg.png?w=300&h=204)
![[fig. 2] ucv6_ucm_cfg ucv6_ucm_cfg](https://tblogbelgium.files.wordpress.com/2011/02/ucv6_ucm_cfg.png?w=300&h=162)
![[fig. 3] ucv6_ent_param_cfg ucv6_ent_param_cfg](https://tblogbelgium.files.wordpress.com/2011/01/ucv6_ent_param_cfg.png?w=300&h=130)
![[fig. 4] ucv6_common_device_profile ucv6_common_device_profile](https://tblogbelgium.files.wordpress.com/2011/01/ucv6_common_device_profile.png?w=259&h=300)
 Cisco BeLux Tweets
Cisco BeLux Tweets tblog BeLux feed
tblog BeLux feed Cisco BeLux Channel
Cisco BeLux Channel